YouTuber Hacked - A Story About Session Hijacking
Published Date: 17/02/2024 Written By: Luke Pettigrew
Not long before writing this post, I noticed a live video by Tesla US on my YouTube homepage. I thought to myself, I don’t ever remember subscribing to Tesla US on YouTube, so I clicked on the video and saw that it had a few thousand viewers. At first glance it appeared to be legit, I then looked at the channel itself, which contained many Tesla videos with legitimate looking view counts and upload dates… but then I spotted the username appeared really strange, it said “@TeslaUS.Corp._News_.”, which is not what you’d expect it to be!
At the time I thought - I’ll just unsubscribe as maybe it was a bug and I don’t have an interest in the brand anyway so I did just that. A day later, I saw a recommended video by a YouTuber (Dave Cam) who I sometimes watch - related to one of my hobbies. It was titled, "How my YouTube channel got hacked!" and being in the Cybersecurity industry, I figured I’d take a look and see what happened to them. Lo and behold, he was a victim of a phishing attack. So how did it happen?
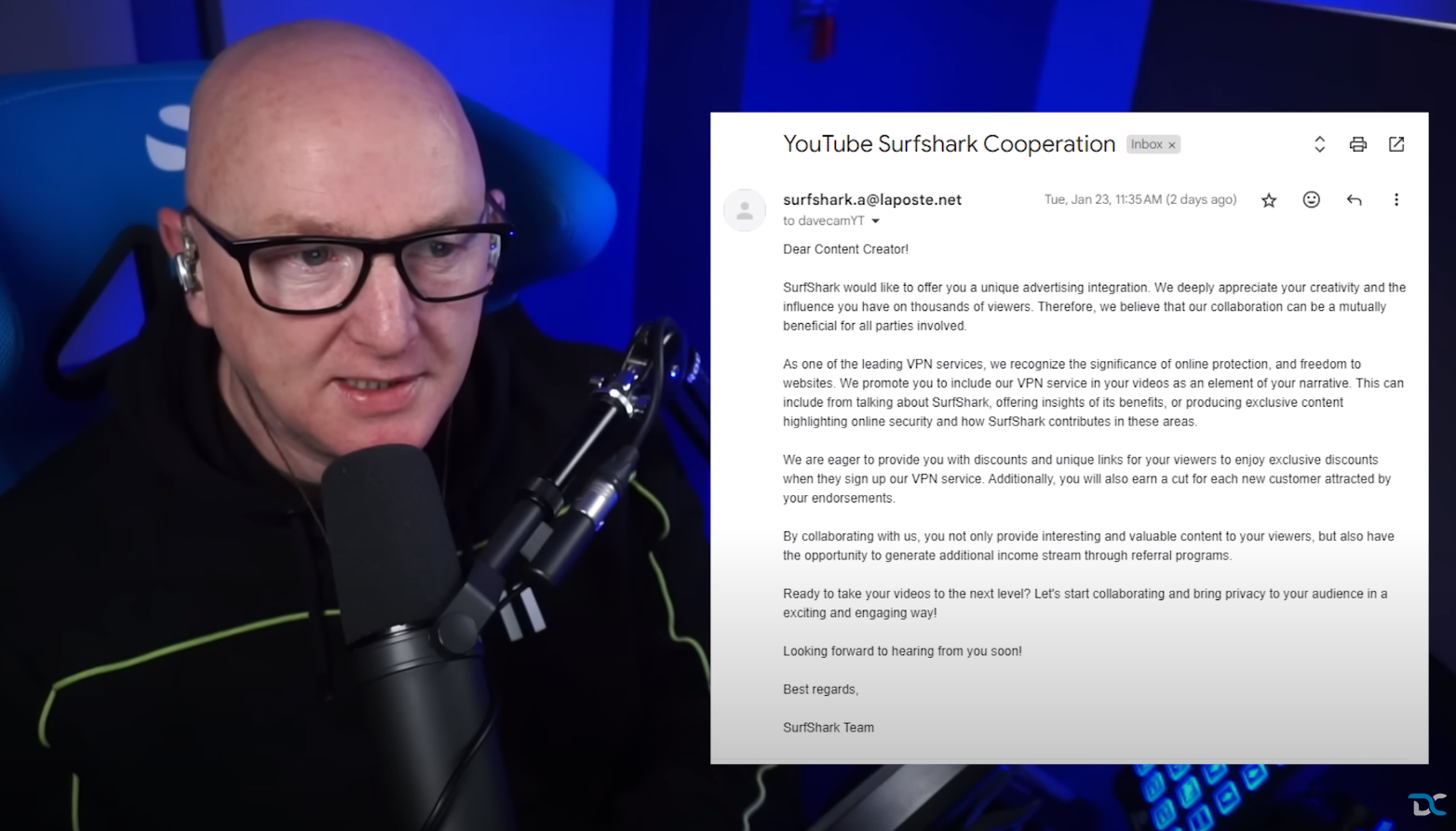
Dave had received an email claiming to be from Surfshark, a well known VPN provider. They were offering him a sponsorship deal as part of his YouTube channel. As he is a relatively small channel, this obviously piqued his interest. He did however notice the email address was a little strange, surfshark.a@laposte.net. (Indicator 1)
A quick Google search would have shown him that this was a French email service provided by the La Poste postal service - a little strange for a company like Surfshark to be using! Those with a keen eye would also notice that the content in the emails body references SurfShark (they’re actually branded as Surfshark) and it having some oddly structured sentences, with some grammatical errors. (Indicator 2)

Image 1. The first email from the cybercriminals
But with it being such a good offer for his YouTube channel, curiosity got the better of him! He replied to the email. A few hours later whilst he was away from his computer, he received an email back. He opened it on his mobile phone… and thought it was pretty believable, though it did contain the offer of $1,800 (Indicator 3) which raised some suspicion and a Dropbox link (Indicator 4) containing some materials that they wanted him to promote them with
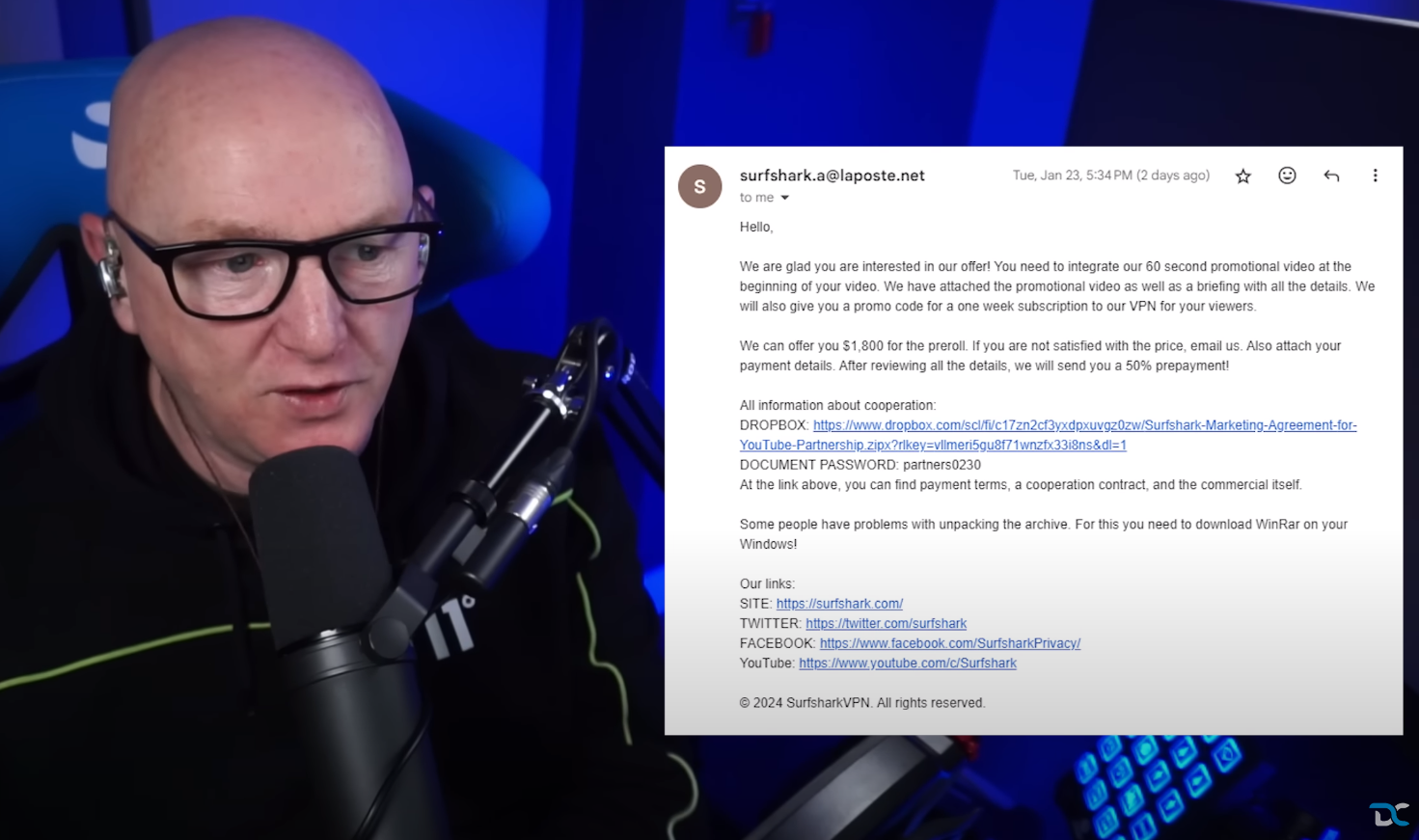
Image 2. The email from the cybercriminals after he had replied.
This time he thought, maybe this isn’t quite right and so he forwarded the email to Surfshark’s “influencers@surfshark.com” which at this point he should have noticed the difference in the email domains. However, he was too impatient to wait for a response from Surfshark to confirm if it was, and so he went ahead and downloaded the ZIP file to check it out. (Indicator 5)
As it was hosted on Dropbox, the download was not scanned for viruses and so he unknowingly downloaded the malicious file. He then extracted and opened the ZIP file; it contained a few files, two of which were a PDF and an MP4 file. The video was a 60 second promo video from Surfshark about affiliate marketing, which somewhat may have settled any concerns he may have had at the time. Then moving on from that he decided to double click on the PDF to read its contents… which later would turn out to be a BIG mistake… but as nothing happened (Indicator 6), he tried opening it again, and again, nothing happened.
Dave assumed there was something wrong with the file so he decided to just carry on with his day and worry about it later, but to his surprise, barely half an hour later he received a notification on his phone saying he was locked out of his Google account, the one linked to his YouTube! At this point he rushed back to his computer and checked the files again, specifically the PDF file. To his surprise, it was actually an EXE (executable) file that was disguised as a PDF file! (Indicator 7)
He even admitted that he was complacent at the time and didn’t check it hard enough, and that he should have scanned the download before interacting with it. What this executable secretly did was take his cookies, session tokens and other files and transferred them over to the hijacker, containing access to all of his social accounts. Meaning they now had complete access to his YouTube channel - even if he had multi-factor enabled!
Dave then reached out to @TeamYouTube on X (Twitter) for support as soon as he noticed, I won’t bore you with all the details on this bit but during the back and forth process of communicating with YouTube’s support - he decided to completely format his computer to try and prevent any further malicious activity, what a huge inconvenience!
Some more time passed until he received a message from someone saying that his channel was now showing as Tesla US. All of his content was gone, and completely replaced with various videos and playlists of the Tesla content, there was even a live stream running on his channel, something these hackers do where they share more phishing links to catch unsuspecting victims, often scams related to cryptocurrencies.
Unfortunately for Dave, this continued throughout the night, I imagine he could not sleep! His channel then became branded as Ripple (a cryptocurrency), with the username of “@Ripple.corpor._” - again live streaming. This time with a deepfake video of Elon Musk promoting the cryptocurrencies and the scams.
The next day, he continued discussions with Google and YouTube when he was finally able to regain access to his accounts and YouTube Channel. Upon his inspection, all of his content was set to private which was very lucky for him. Though everything else was changed from his brand name and imagery to something else! They hadn’t changed his Google AdSense though which meant for him, his income from ads were somewhat unaffected, though it did mean he lost approximately 1,700 subscribers in less than 24 hours! (Including myself, though I have since resubscribed…)
Dave then explained how it made him feel embarrassed, and like he had been robbed or burgled but in this case that they’d taken over his home! This attack wasn’t fully over yet though as when he took to X (Twitter) to post about what had happened, he was inundated with bots trying to gain access to his account - though this time he was well aware of what was happening.
As he then explained, his nightmare over the course of 24 hours could have been avoided if he had recognised the signs and had checked things more thoroughly - better still, had waited for a response from Surfshark themselves to confirm its legitimacy. His advice to other YouTubers is to check things over multiple times before you even think about interacting with it.
Now this is not a new type of attack, nor is he the only YouTuber to experience it. Linus Tech Tips released a video titled, “My Channel Was Deleted Last Night”, where they were victim of a very similar thing back in March 2023. In other scenarios like this one, the cybercriminals use Redline Infostealer malware, a tool that allows them to do this type of attack very easily, in Dave’s case they may or may not have used the same but it would have been very similar if not!
A recap of the Indicators to look out for 👀
Is the sender's email address legitimate, does it match the businesses typical sender domain.
Does the email contain grammatical errors, like misspelt words, or slightly-off brand names.
Is there an emotional trigger like a money incentive, or a matter of urgency.
Does the email contain a link or attachment, often a ZIP file hosted externally.
Avoid downloading attachments that you’re not fully sure of, scan them first or contact the sender directly, or your IT department.
If there is an unexpected behaviour like opening the file appears to do nothing or not what it would typically do, this should raise alarm bells.
Double check the file is actually what it says it is, if you're unsure - ask a friend or your IT department to check it over.
This is a reminder that phishing emails and social engineering can often be a really easy way in for cybercriminals, especially to someone who may not be too familiar with this type of stuff! In this case it was to gain access to a YouTubers channel and social accounts, largely to trick more unsuspecting victims with crypto scams.
In other scenarios and for a business, this type of attack could be done to gain access to your business’s communication tools, to gather information, access confidential data and much much more. Though we’d like to think that if you have security tooling that the malware would be detected and stopped before anything bad can happen - though not everyone will have these mechanisms in place, and they don’t always catch it.
This story shows why it’s so important to help and teach people how to spot a phishing email, and the right steps to take to avoid becoming a victim.